Identity Provider
The OneCloud platform supports managing multiple identity provider, such as LDAP, Dingtalk, Lark, WeCom, etc. to enable login to the OneCloud platform via third-party app authentication.
Enterprise users use OneCloud platform process
- Import users to the
OneCloud
platform.
- Local users (SQL source): The platform has a built-in SQL source, no configuration is required at the Identity Provider, just create a new user in the user list to create or import users.
- LDAP user: new Identity Provider for LDAP authentication protocol, after the setting is finished, it will synchronize the users on LDAP server to OneCloud platform.
- Other identity provider (identity provider other than LDAP and SQL authentication protocols): Create new identity provider other than LDAP authentication protocols, and you need to check the box to create users automatically. This method will not create users immediately, but will automatically create users with the same name on the platform when they log in to the OneCloud platform with the corresponding Identity Provider method.
- Logging into the
OneCloud
platform.
- Enterprise users who have configured only SQL or LDAP authentication protocols can only log in to the OneCloud platform by username and password on the login page.
- When enterprises configure other identity provider (identity provider other than LDAP and SQL authentication protocols), there are two cases.
- When other identity provider are configured with auto-create users checked, the Identity Provider can be used as the primary Identity Provider, and enterprise users can select the corresponding Identity Provider icon on the login page to authenticate to the OneCloud platform through the corresponding Identity Provider method and automatically create users with the same name on the platform.
- When other identity provider are configured without automatically creating users, the Identity Provider is used as a secondary Identity Provider, and local users can associate their user information with this Identity Provider. After successful association, enterprise users can select the corresponding Identity Provider icon on the login page and authenticate to the OneCloud platform by the corresponding Identity Provider method.
Description
- Main Identity Provider: The Identity Provider defines the source of the user. sql and LDAP identity provider are the main Identity Provider by default. Other identity provider can be used as the primary Identity Provider if “auto-create users” is enabled when adding.
- Auxiliary Identity Provider: the Identity Provider is only used as the authentication login method, the user of the main Identity Provider needs to associate with the auxiliary Identity Provider first, after successful association, you can use the Identity Provider to login to the platform.
Entry: In the cloud management platform, click the top left corner of  navigation menu, and click “IAM & Security/IAM/Certification Source” menu item in the left menu bar that pops up to enter the Identity Provider page.
navigation menu, and click “IAM & Security/IAM/Certification Source” menu item in the left menu bar that pops up to enter the Identity Provider page.
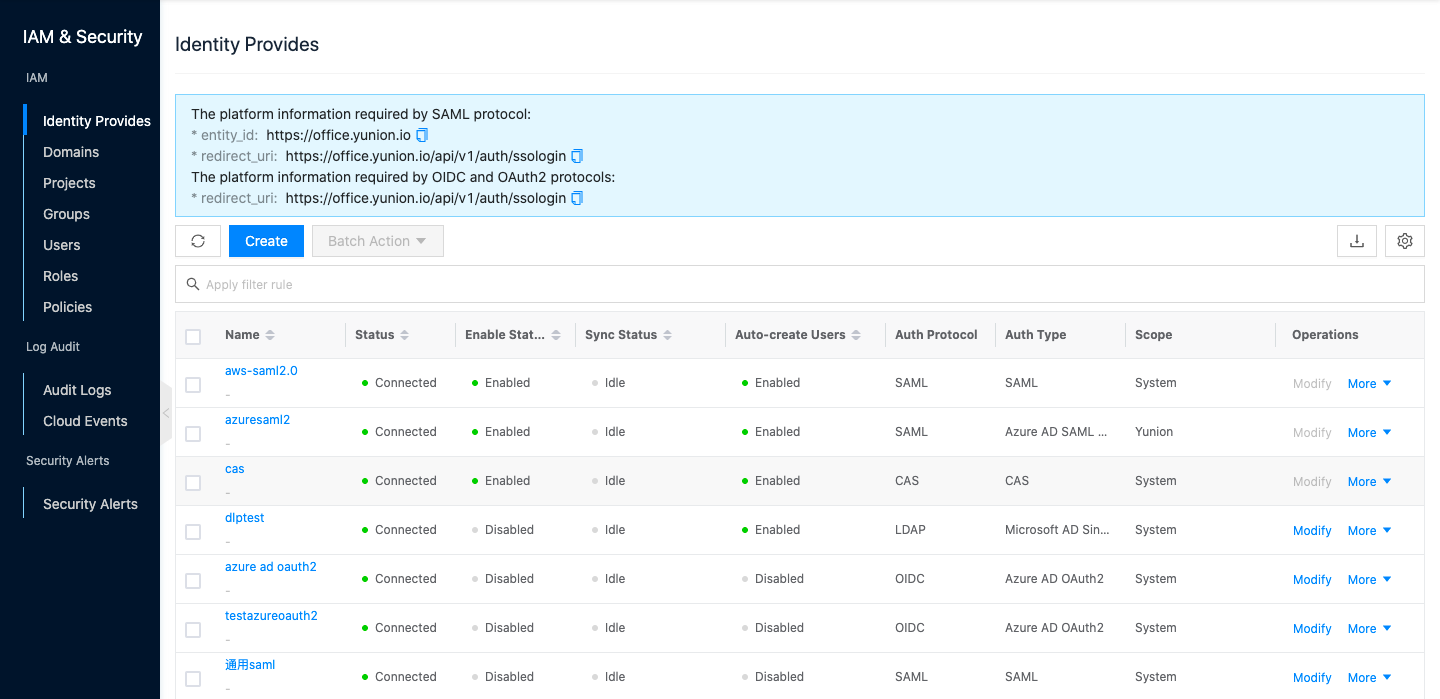
Description
The top of the list will show the SAML protocol and the EntityID and Redirect_url (callback address) that the OIDC and OAuth2 protocols require from the platform and support replication.
Create Identity Provider
This function is used to interface with third-party identity provider.
Create Identity Provider for LDAP protocol
Make sure that an LDAP server exists in the user’s environment.
- On the Identity Provider page, click the “Create” button at the top of the list to enter the Create Identity Provider page.
- Configure the following parameters.
- Identity Provider Attribution: Set the attribution range of the Identity Provider. When the Identity Provider belongs to the system, that is, all users in the system can use the Identity Provider to log in to the platform. When the Identity Provider belongs to the domain, only the users in the domain can use the Identity Provider to log in to the platform. In the Domain View, the Identity Provider belongs to the domain administrator’s domain.
- Name: The name of the Identity Provider.
- Authentication protocol: Select “LDAP”.
- Authentication type: Support importing single domain from Microsoft Active Diretory, importing multiple domains from Microsoft Active Diretory, importing single domain from OpenLDAP/FreeIPA. The configuration parameters are slightly different for different authentication types.
- When the authentication type is Microsoft Active Diretory Import Domain.
- User attribution target Domain: Optional, select the domain that the user belongs to on the LDAP server in the cloud management platform.
- Server address: the URL address to build the AD domain control server in the format of ldap(s):// server IP address, must start with ldap:// or ldaps://.
- Basic DN: DN is Distinguished Name, basic DN is the unique name identification of the entry in the whole directory tree. The format is “DC=xx,DC=com”
- User name: The user name to connect to the AD domain control server.
- Password: the corresponding password of the user who connects to AD domain control server.
- User DN: User DN is the root path to find users in the LDAP directory, users will be found recursively under this root path, the format is “CN=users,OU=xx,DC=xx,DC=com”.
- Group DN: The group DN is the root path to find groups in LDAP directory, and will recursively find groups under this root path in the format of “CN=groups,OU=xx,DC=xx,DC=com”.
- User Enable Status: Set the status of the user imported from the Identity Provider. When set to Enable, the user can log in to the system, and Disable, the user cannot log in to the system.
- When the authentication type is Microsoft Active Diretory import multiple domains (when the Identity Provider belongs to the domain, setting this item is not supported).
- Server address, basic DN, user name and password are the same as importing a single domain.
- Domain DN: The domain corresponds to the OU (organization) in LDAP, the domain DN is the root path for LDAP to find the domain, and will find all domains under this path. The format is “OU=xx,DC=xx,DC=com”.
- User Enable Status: Set the status of the user imported from the Identity Provider, when set to Enable, the user can log in to the system, when disabled, the user cannot log in to the system.
- When the authentication type is OpenLDAP/FreeIPA import single domain.
- Target domain: Optional, select the domain on the LDAP server to which the user belongs in the cloud management platform.
- Server Address: The URL address to build the OpenLDAP or FreeIPA server, in the format of ldap(s):// server IP address, must start with ldap:// or ldaps://.
- Basic DN: DN is Distinguished Name, basic DN is the unique name identification of the entry in the whole directory tree. The format is “DC=ocdc,DC=com”
- User name: The UID of the user who connects to the server, the format is “UID=admin,CN=users,CN=xx,DC=xx,DC=com”.
- Password: The password of the corresponding user.
- User DN: User DN is the root path to find users in LDAP directory, and will recursively find users under this root path in the format of “CN=users,OU=xx,DC=xx,DC=com”.
- Group DN: The group DN is the root path to find groups in the LDAP directory, and will recursively find groups under this root path in the format “CN=groups,OU=xx,DC=xx,DC=com”
- User Enable Status: Set the status of the user imported from the Identity Provider, when set to Enable, the user can log in to the system, if disabled, the user cannot log in to the system.
- Click the “OK” button to create a new Identity Provider.
Create Identity Provider for CAS
-
On the Identity Provider page, click the “Create” button at the top of the list to enter the Create Identity Provider page.
-
Configure the following parameters.
- Identity Provider attribution: Set the attribution range of the Identity Provider. When the Identity Provider is attributed to the system, that is, all users in the system can use the Identity Provider to log in to the platform. When the Identity Provider belongs to the domain, only the users in the domain can use the Identity Provider to log in to the platform. In the Domain View, the Identity Provider belongs to the domain administrator’s domain.
- Name: The name of the Identity Provider.
- Authentication protocol: Select “CAS”.
- Authentication type: Support CAS.
- CAS service address: URL address of CAS single sign-on server, such as http://cas.example.io/cas.
- User ID: Set the corresponding user ID attribute in the CAS, usually cas:user, please change it if there is any change.
- User name: Set the corresponding user name attribute in the CAS, usually cas:user, please change this item if there is any change.
- Auto-create user: When auto-create user is checked, a local user will be automatically created in the system for users who log in for the first time through the Identity Provider. When this item is not checked, the Identity Provider is used as a secondary Identity Provider and the user needs to be associated with the Identity Provider to log in to the platform through the Identity Provider.
- User attribution target Domain: You need to set this parameter only after checking the box to automatically create users. Select the domain to which the user automatically created by this authentication method logs in. When the Identity Provider belongs to the domain, the user belongs to the target domain and the Identity Provider belongs to the same domain and cannot be changed.
Advanced configuration: Hidden by default, can be configured according to requirements.
- Default project: Set the default project to be added by users who log in through CAS Identity Provider and created automatically in the platform. When selecting “Psee use the project in CAS”, you need to specify the field name of the added project, such as cas:proj, etc. If there is a matching project in the cloud management platform, the user will be added to the corresponding project directly, and if there is no matching project, the project with the same name will be created automatically.
- Default role: Set the default role for users who log in through CAS Identity Provider and are automatically created in the platform to join the project. When selecting “Psee use role in CAS”, you need to specify the field name of the role, such as cas:role, etc. If there is a matching role in the cloud management platform, the corresponding role will be used directly to join the project. If there is no matching role, the default role will be used to join the project.
- Display name: Set the corresponding display name field in the CAS.
- Email: Set the corresponding mailbox field in the CAS.
- Mobile: Set the corresponding cell phone number field in the CAS.
-
Click the “OK” button to connect the Identity Provides and synchronize the domain, group and user information on the Identity Provides.
Create Identity Provides for SAML authentication protocol
-
On the Identity Provides page, click the “Create” button at the top of the list to enter the Create Identity Provides page.
-
Configure the following parameters.
- Identity Provider attribution: Set the attribution range of the Identity Provider. When the Identity Provider is attributed to the system, that is, all users in the system can use the Identity Provider to log in to the platform. When the Identity Provider belongs to the domain, only the users in the domain can use the Identity Provider to log in to the platform. In the Domain View, the Identity Provider belongs to the domain administrator’s domain.
- Name: The name of the Identity Provider.
- Authentication protocol: Select “SAML”.
- Authentication type: Support SAML and Azure AD SAML2.0. different parameters are supported for different types.
- When the authentication type is SAML, please refer to
- Supports uploading SAML IDP metedata files or manual form entry to configure parameters.
- User ID: Set the corresponding user ID attribute in the SAML.
- User name: Set the corresponding user name attribute in the SAML.
- When the authentication type is Azure AD SAML2.0, only TenantId needs to be configured. please see How to get Azure AD SAML2.0 related parameters?
- User attribution target Domain: you need to set this parameter only after checking the box for automatic user creation. When the Identity Provider belongs to the domain, the user belongs to the same domain as the Identity Provider, and cannot be changed.
Advanced configuration: Hidden by default, can be configured according to requirements.
- Default project: Set the default project for users who log in through the Identity Provider of SAML authentication protocol and are automatically created in the platform to join.
- Default Role: Set the default role joined by users who log in through the Identity Provider of SAML authentication protocol and created automatically in the platform.
How to get SAML related parameters?
Configure AWS SSO as SAML IDP for AWS SSO is the platform’s SAML IDP, and is currently only supported in AWS International.
-
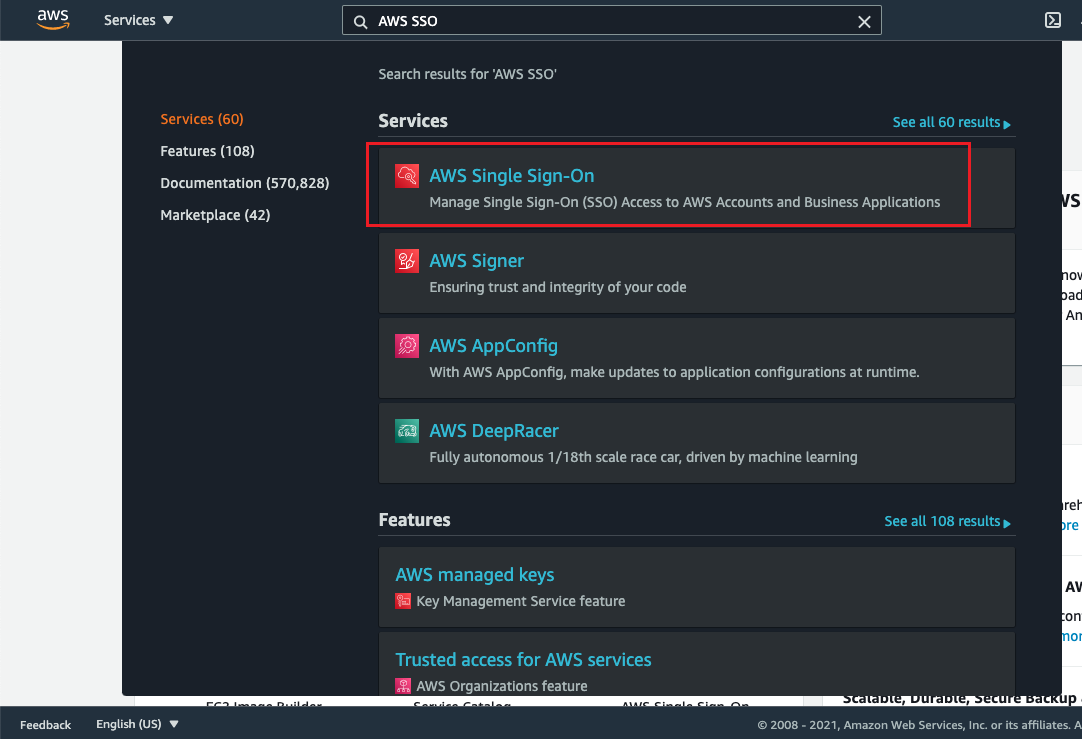
Search for “AWS SSO” on the AWS platform and go to the “AWS Single Sign-On” page.
-
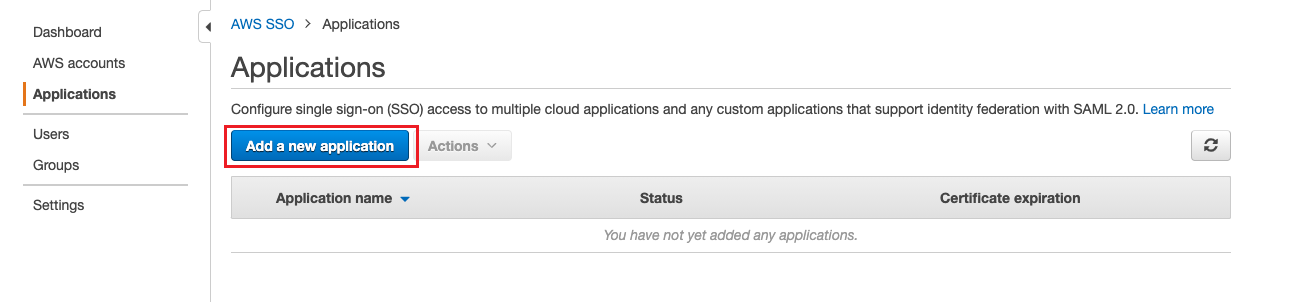
In Applications page,add a new application.
-
Select “Add a custom SAML 2.0 application” to go to the “Configure Custom SAML 2.0 application” page.

-
Download the AWS SSO SAML metadata file, which is the XML file of the “SAML IDP metadata” required to configure the SAML in the OneCloud platform.
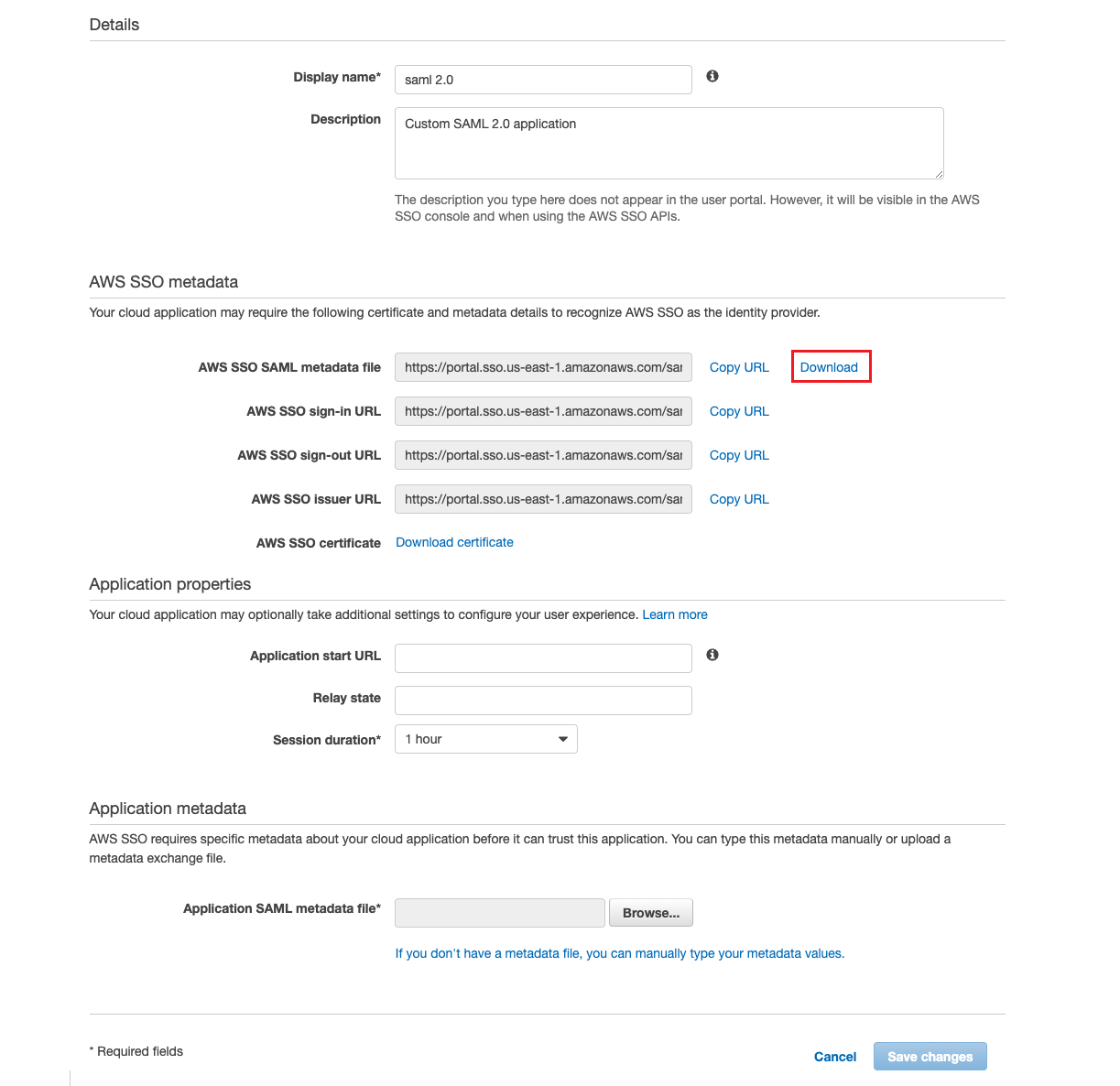
-
Choose to upload Application SAML metadata file or type the metadata values manually in the application metadata.
-
Application SAML metadata file:
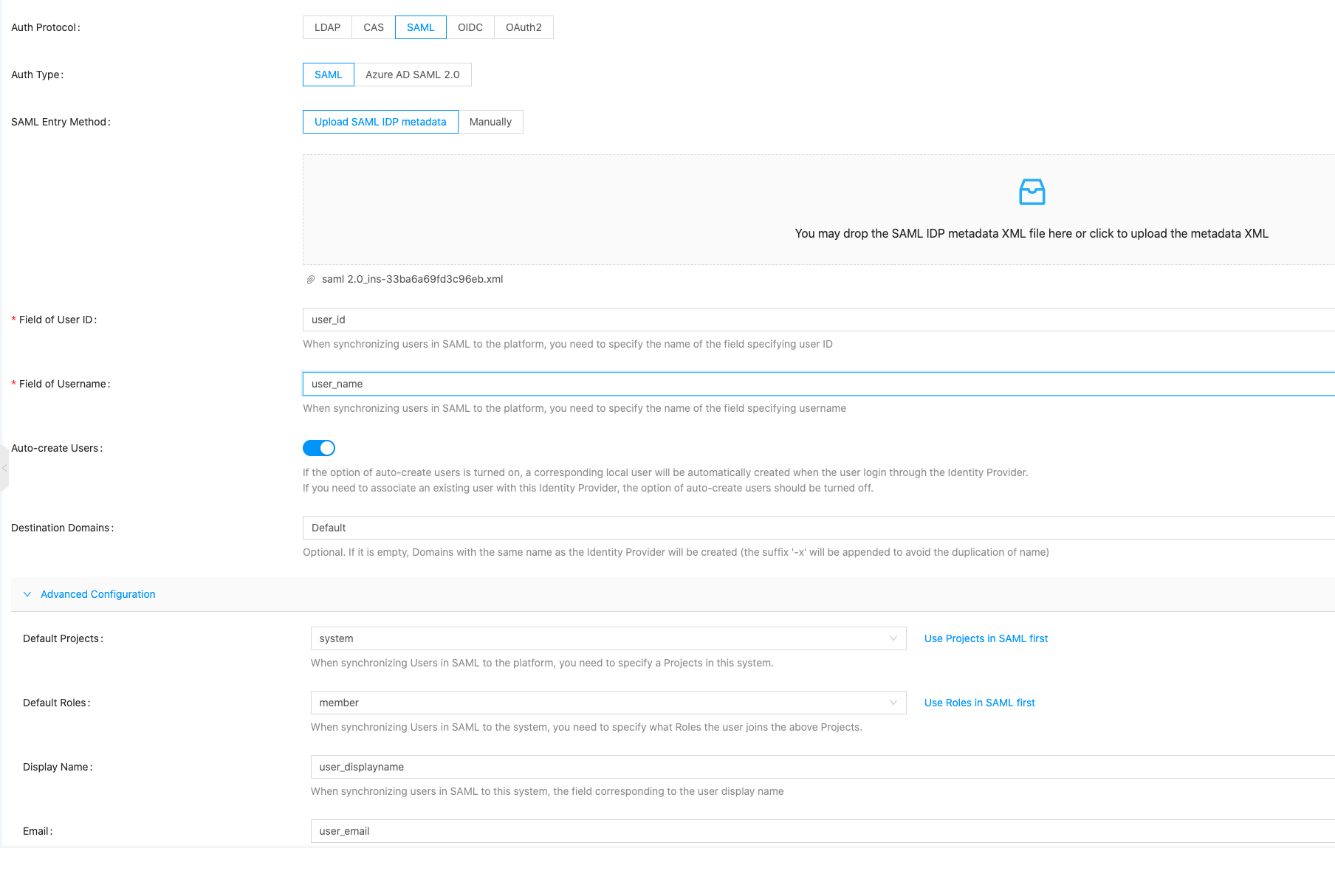
- Create a new identity providers on OneCloud platform, select “SAML” as the authentication protocol and “SAML” as the authentication type.
- Select “Upload SAML IDP metadata” as the SAML entry method, and upload the AWS SSO SAML metadata file downloaded from AWS.
- User ID, User Name: Set the user attributes of user ID and user name, such as user_id, user_name, and you need to map the application properties to the user properties in AWS SSO in the AWS SAML application properties mapping tab.
- It is recommended to check the box “Create users automatically” and select the domain, project, role, etc. to which the user belongs.
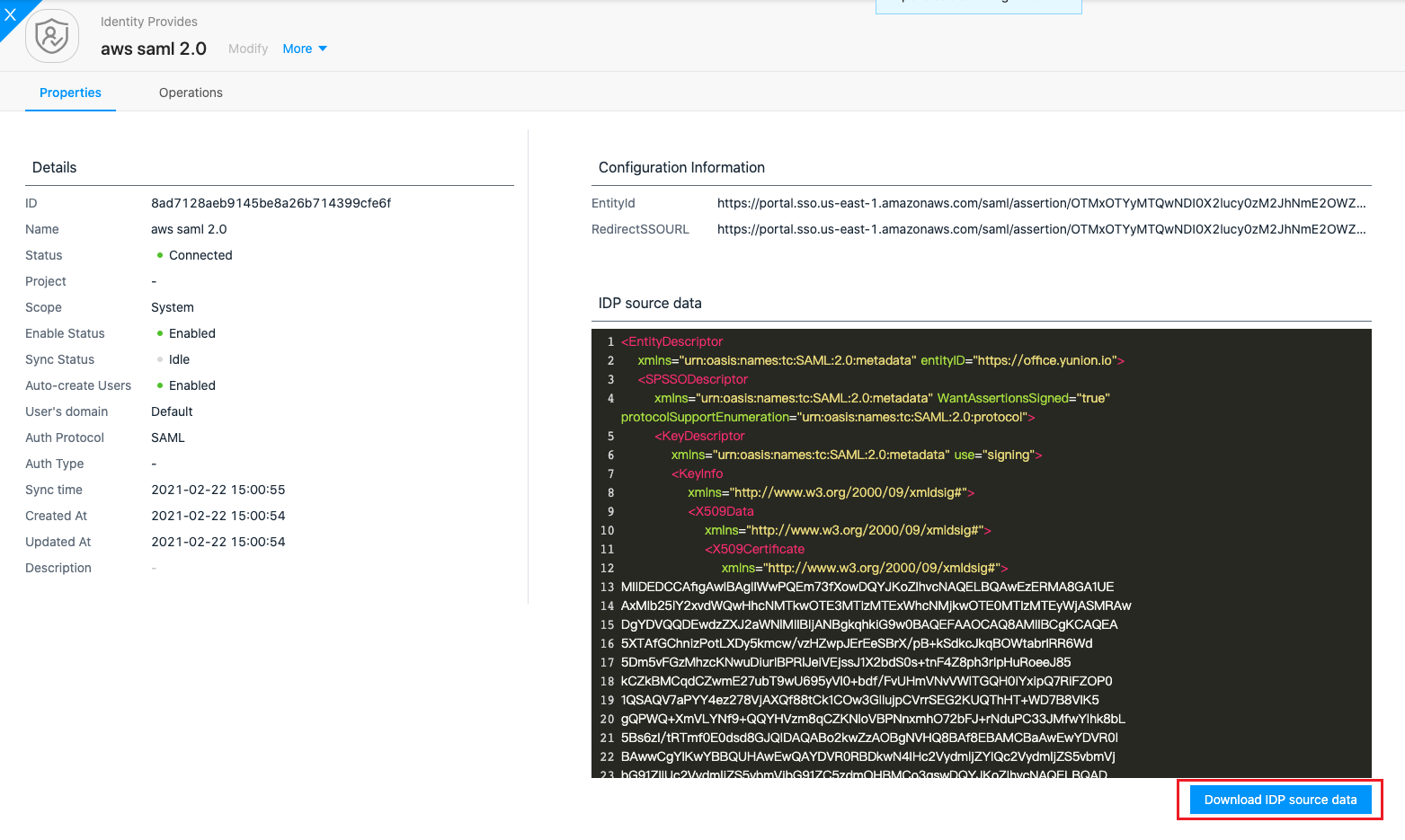
- Download the IDP source data in the identity providers details of the SAML, which is the metadata file needed to configure the SAML application for AWS.
-
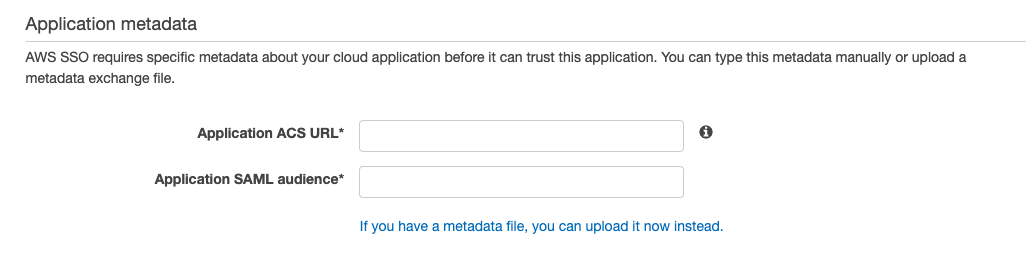
SAML metadata values: In the OneCloud platform’s identity providers list page, Check the platform information required by SAML protocol: redirect_uri is the application ACS URL; the entity_id is the Application SAML audience.

-
-
When the configuration is complete, save the changes.
-
In Application Details - Attribute Mapping, configure the following information and click the “Save Changes” button.

-
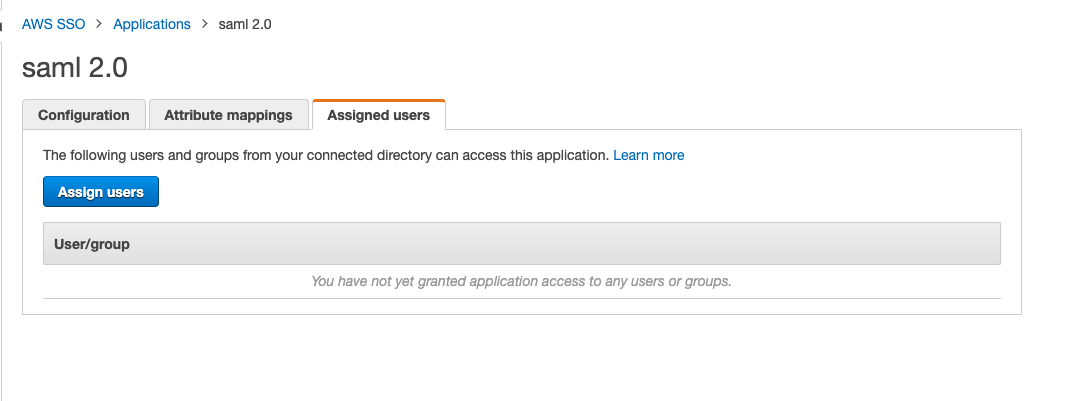
In Application Details - Assigned Users, add the specified users and groups. The added users can access the application through AWS SAML.
How to get Azure AD SAML2.0 related parameters?
-
User login to Azure.
-
To create application in Azure Active Directory - Enterprise Applications - All Applications.

-
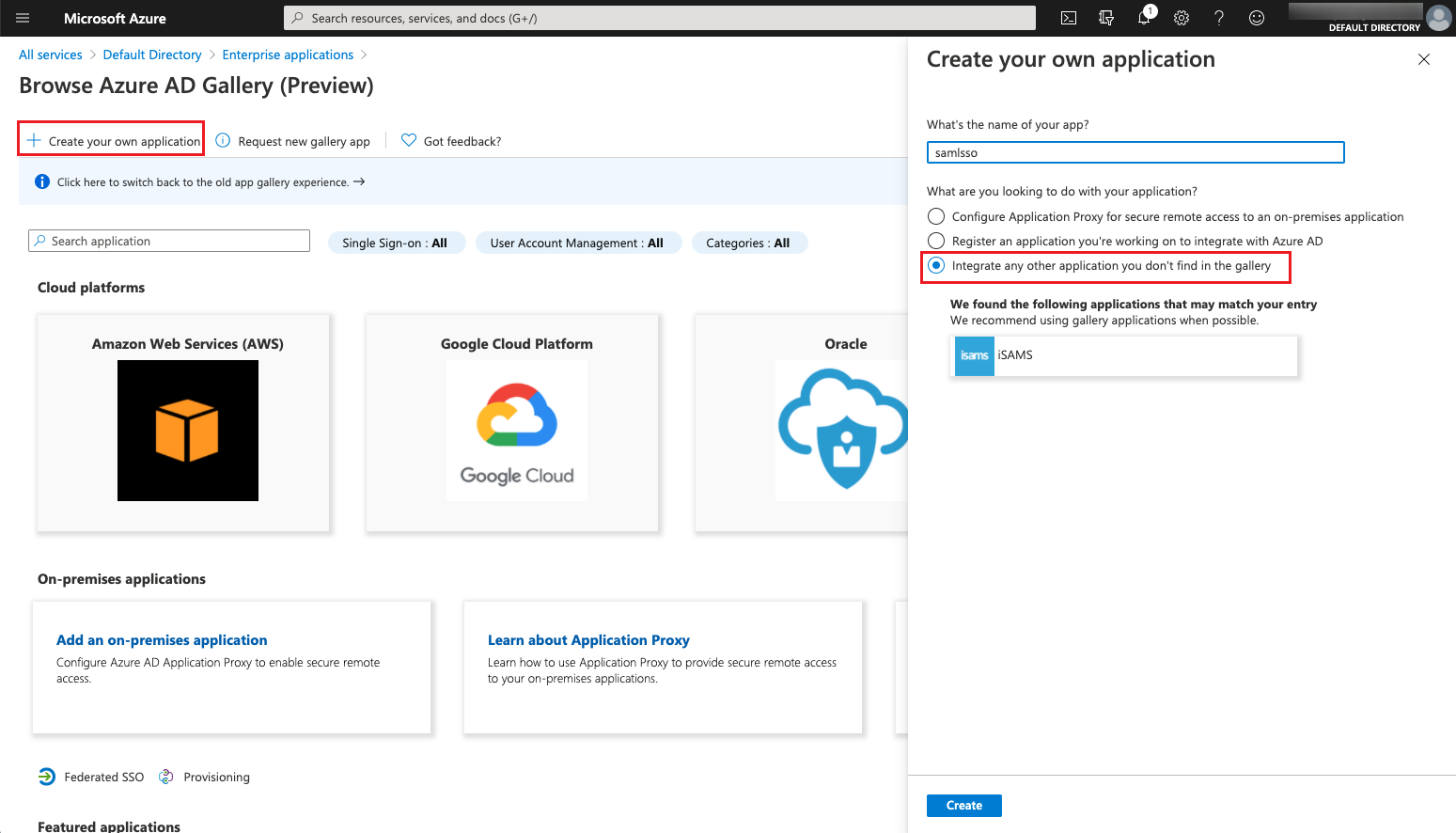
Click the “Create your own application” button to create SAML app. After selecting “Integrate any other application you don’t find in the gallery”, configure the name and create the application.
-
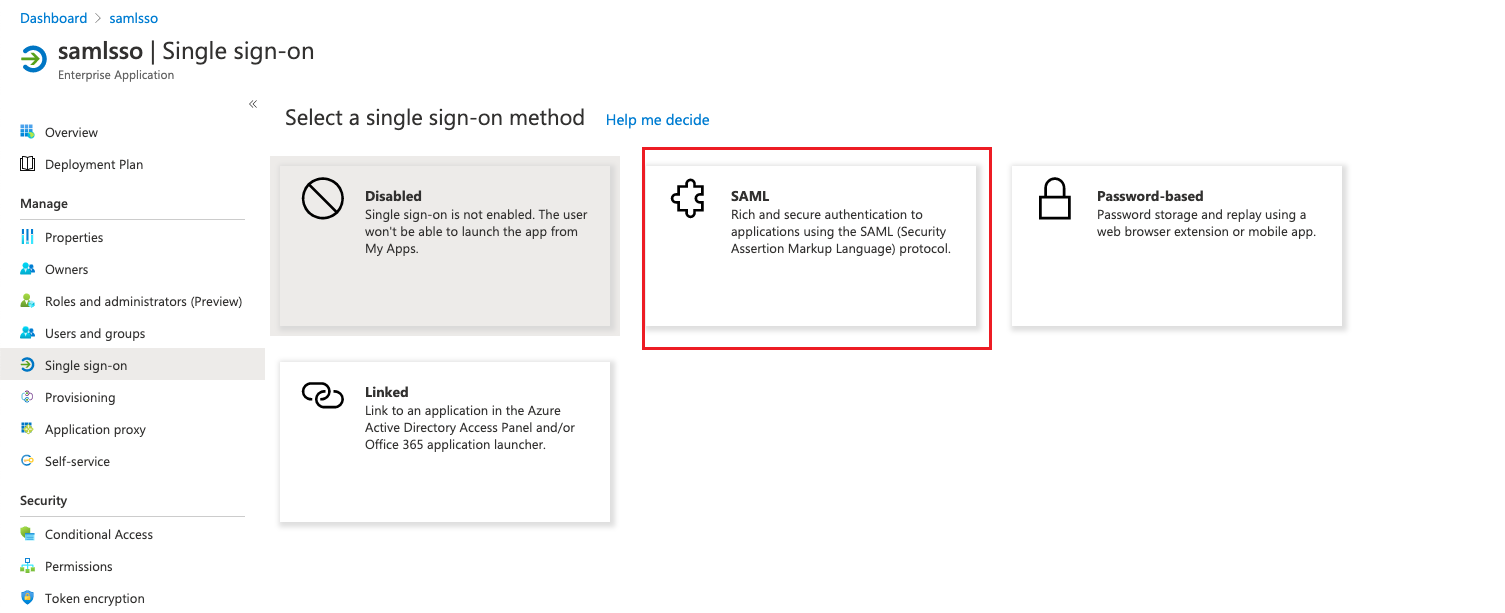
After successfully creating the application, go to the application details and select SAML on the single sign-on page.
-
Configure the identifier ID and reply URL on the Set up Single Sign-On with SAML page;
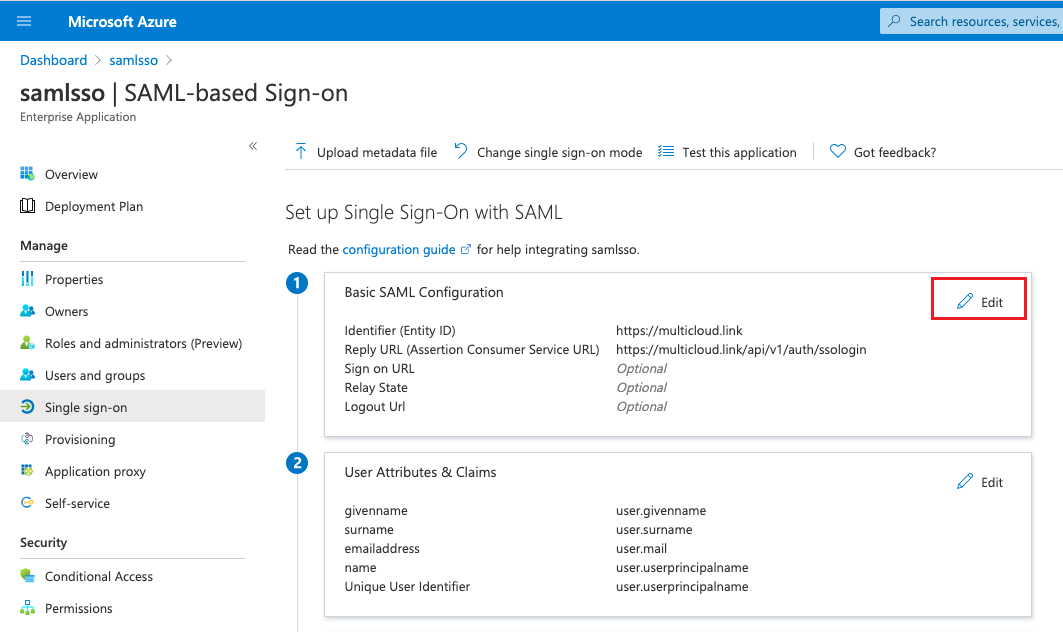
Description
The platform’s Identifier (Entity ID) and dentifier (Entity ID) can be viewed on the OneCloud platform Identity Provider page.
-
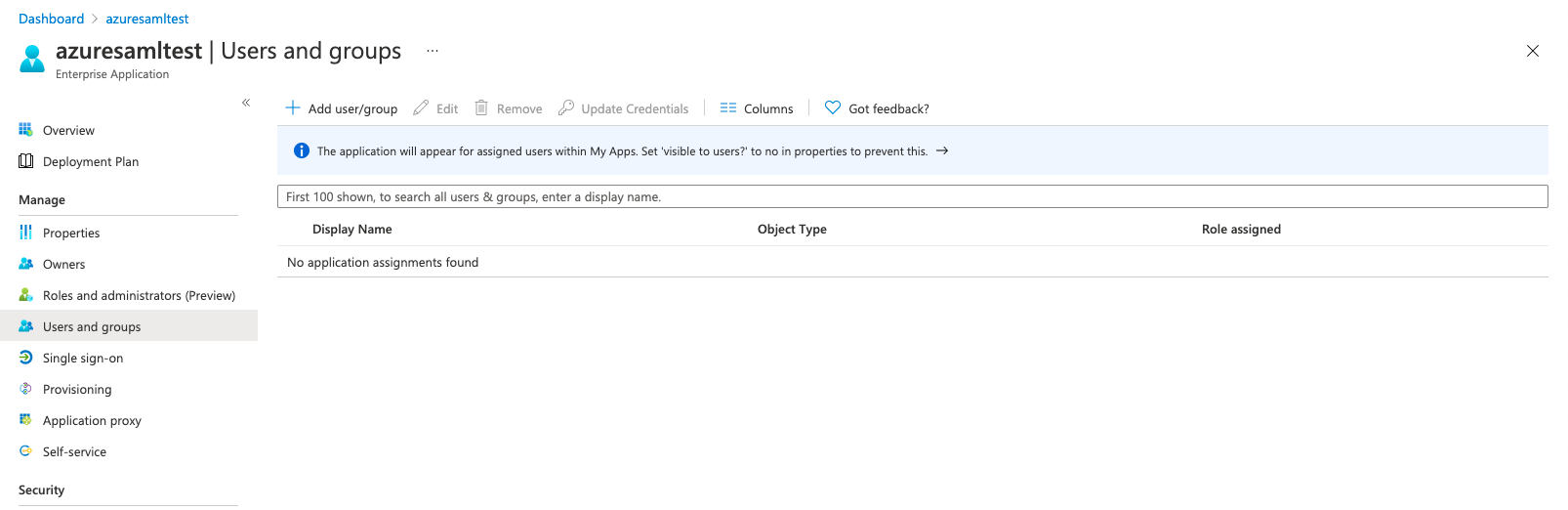
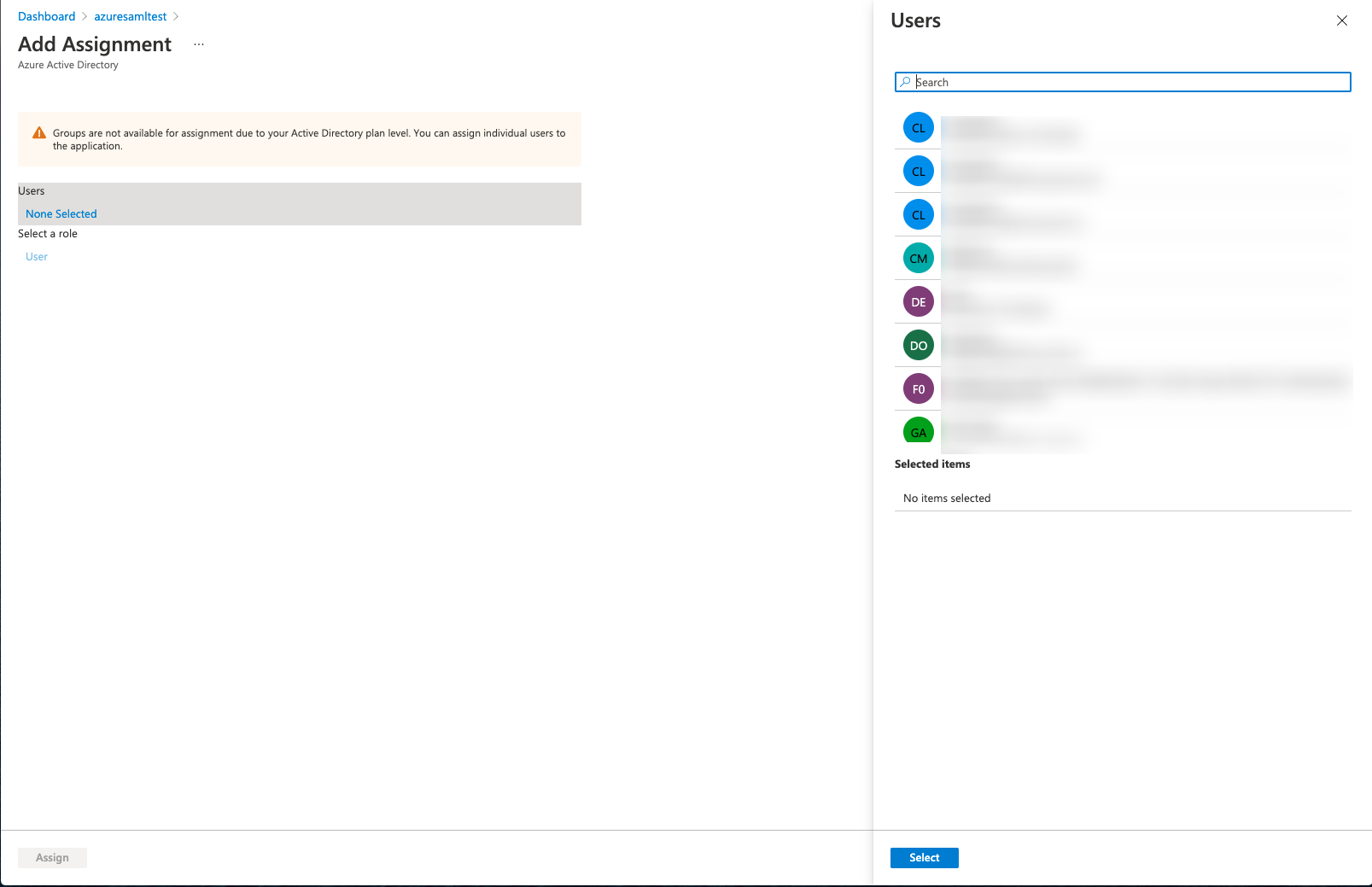
On the Application Details - Users and Groups page, click the “Add User/Group” button to go to the Add Assignment page.
-
After selecting the corresponding users, click the “Assign” button to add the users who need to log in to the platform via the Azure SAML authentication source to the application.
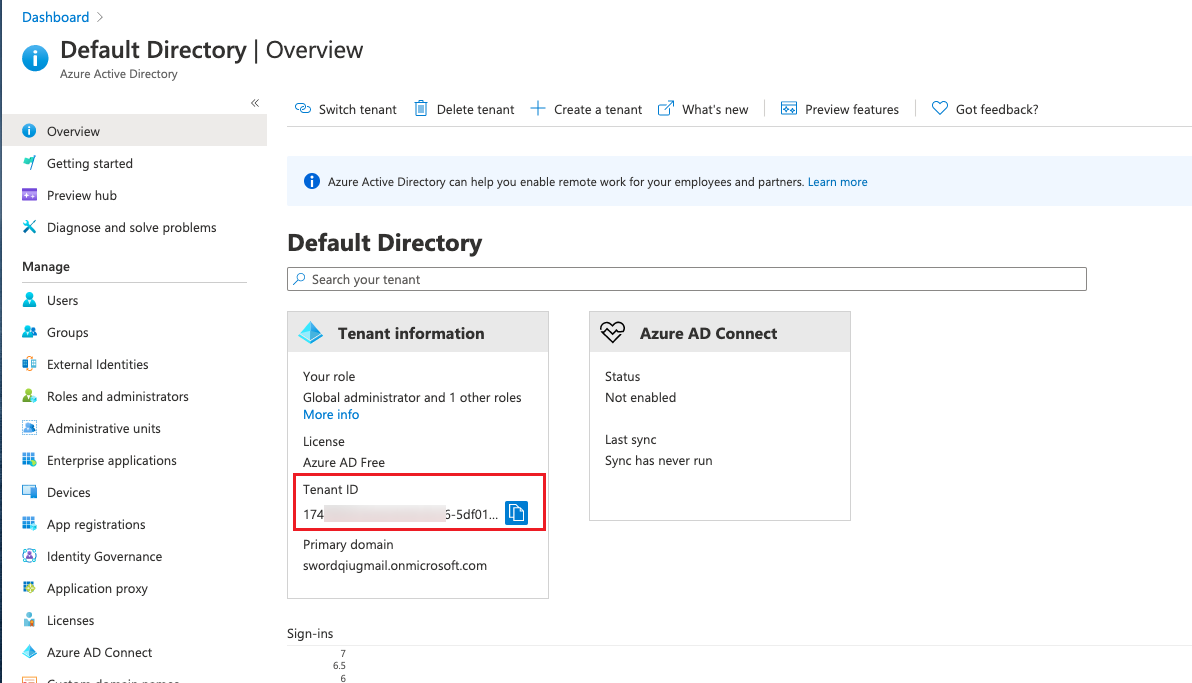
The TenantID (tenant ID) is available on the Azure Active Directory - Overview page.
Create Identity Provider for OIDC
-
On the Identity Provider page, click the “Create” button at the top of the list to enter the Create Identity Provider page.
-
Configure the following parameters.
- Identity Provider attribution: Set the attribution range of the Identity Provider. When the Identity Provider is attributed to the system, all users in the system can use the Identity Provider to log in to the platform. When the Identity Provider belongs to the domain, only the users in the domain can use the Identity Provider to log in to the platform. In the Domain View, the Identity Provider belongs to the domain administrator’s domain.
- Name: The name of the Identity Provider.
- Authentication protocol: Select “OIDC”.
- Authentication type: Support OIDC, Github, Azure AD OAuth2. Different authentication types are configured with different parameters.
- When the authentication type is OIDC: this function requires the existence of OIDC server in the user’s environment, etc.
- ClientID: an identification id of the third-party application, this information is usually public information, used to distinguish which third-party application.
- ClientSecret: the private key information of the third-party application, this information is private information, not allowed to pass in the OAuth2 process, used for security detection and encryption.
- Endpoint: Endpoint that contains all the configuration information required by the OIDC protocol. If the Endpoint information exists, you can directly check the I have Endpoint and fill in the information. If Endpoint information does not exist, you need to fill in Scopes (authorization scope), AuthUrl, TokenUrl, UserinfoUrl.
- User ID: Set the corresponding user ID property in the OIDC, usually name, please change this item if there is a change.
- User name: Set the corresponding user name attribute in the OIDC, usually name, please change this item if there is any change.
- When the authentication type is Github, you need to configure ClientID and ClientSecret. Please see How to get Github related parameters?
- When the authentication type is Azure AD OAuth2, you need to select the CloudEnv where Azure is located (China or global zone), configure ClientID, ClientSecret, TenantID and so on. Please see How to get Azure AD OAuth2 related parameters?
- User attribution target Domain: you need to set this parameter only after you check the box to automatically create users. When the Identity Provider belongs to the domain, the user belongs to the same domain as the Identity Provider, and cannot be changed.
Advanced configuration: hidden by default, can be configured according to demand.
- Default project: Set the default project for users who log in through the Identity Provider of the OIDC authentication protocol and are automatically created in the platform to join.
- Default Role: Set the default role joined by users logged in through the Identity Provider of OIDC authentication protocol and created automatically in the platform.
How to get Github related parameters?
-
user login Github
-
Create an OAuth application in the User Information-setting-Developersetting-OAuth2 Apps page.
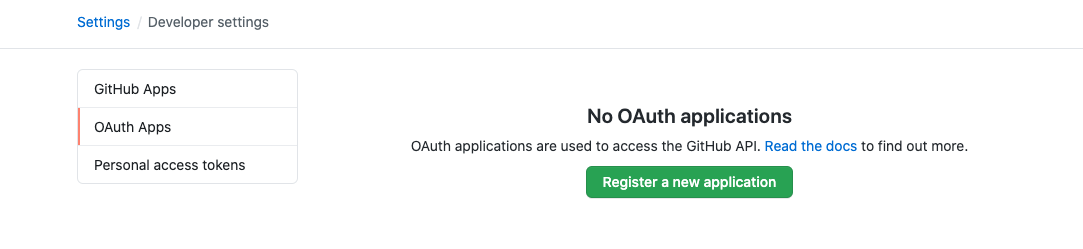
-
Configure the platform access address and the callback address as “https://
/api/v1/auth/ssologin”.
Description
- Set the platform to domain access, and set the access domain in Global Settings - Console Address.
- The platform’s callback address can be viewed on the OneCloud platform Identity Provider page.
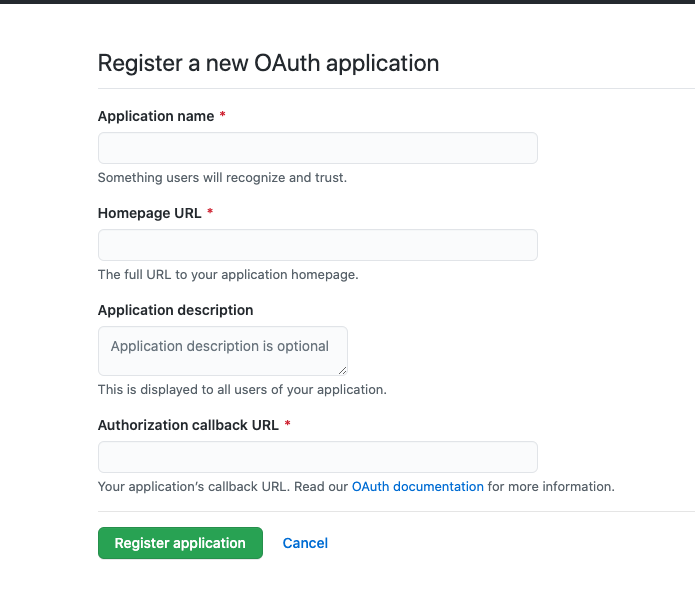
-
Get the ClientID and ClientSecret after successful creation.
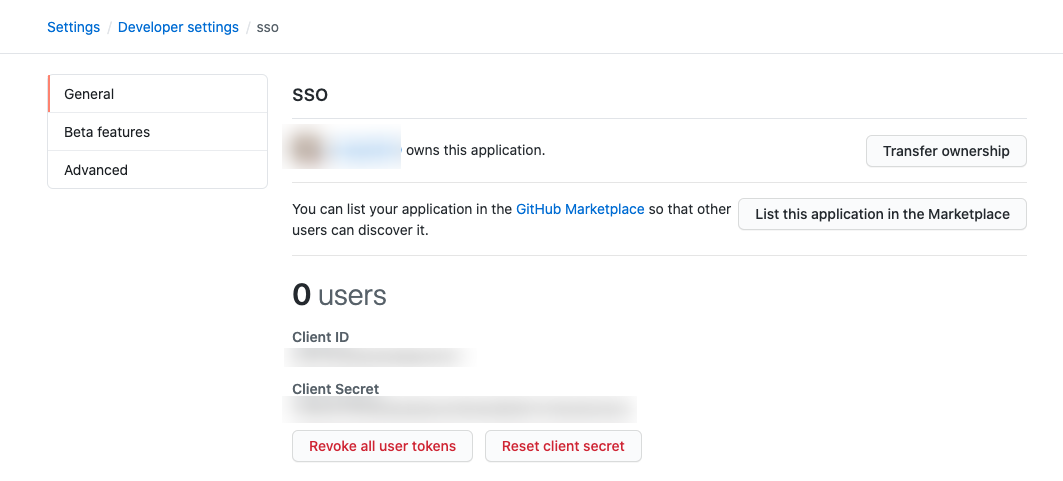
How to get Azure AD OAuth2 related parameters?
-
User login to Azure China or Azure. Take Azure China as an example to introduce how to get the parameters.
-
On the Azure Active Directory-App registrations page, Click the “New Registrations” button to register an application.
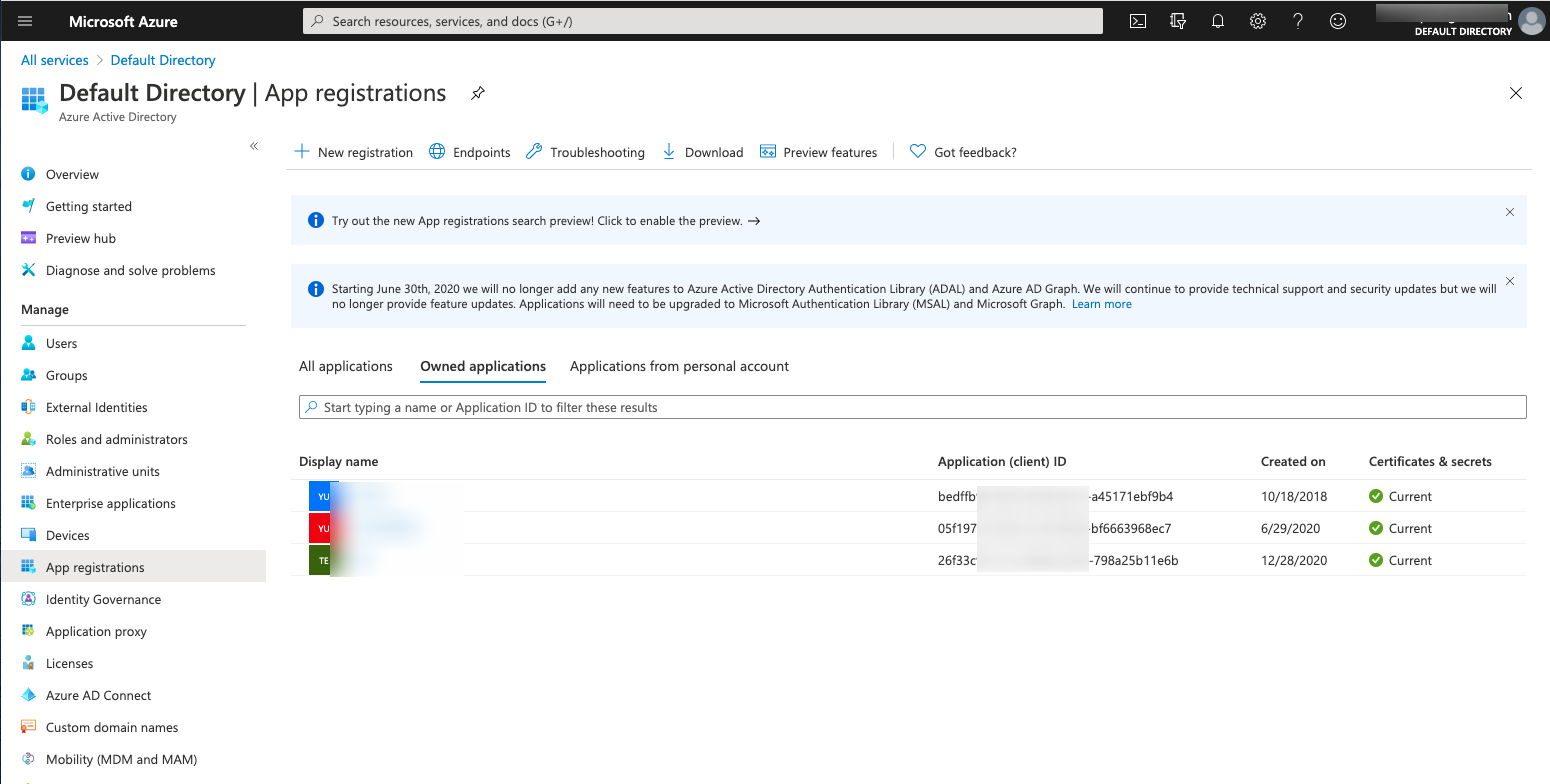
-
Select the supported account types, configure the redirect URI to “web” and the platform callback address to “https://
/api/v1/auth/ssologin” according to the requirements.
Description
- Set the platform to domain access, set the access domain in Global Settings - Console Address.
- The platform’s callback address can be viewed on the OneCloud platform Identity Provider page.
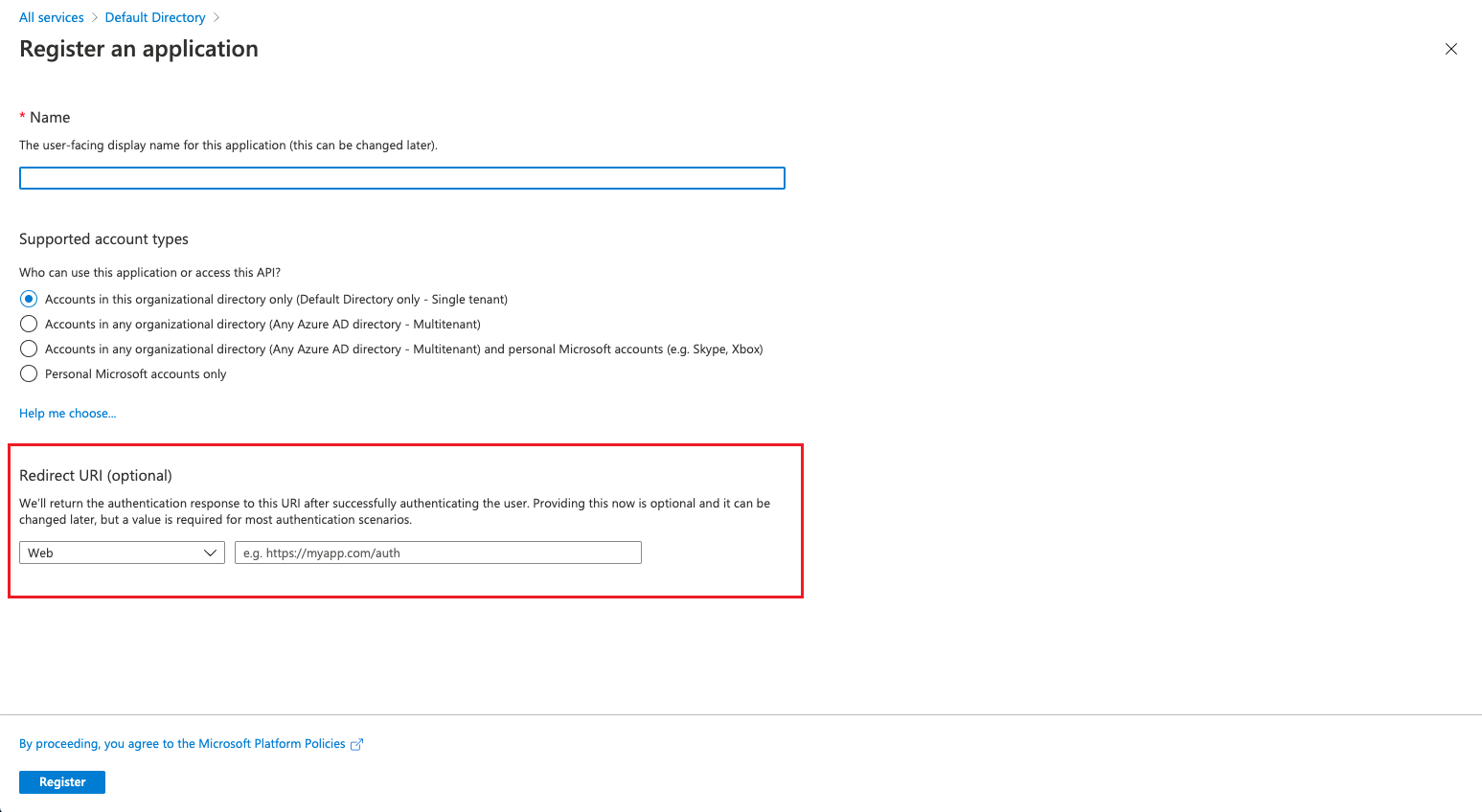
-
After successful creation, the application details page will be entered by default to get ClientID and TenantID .

-
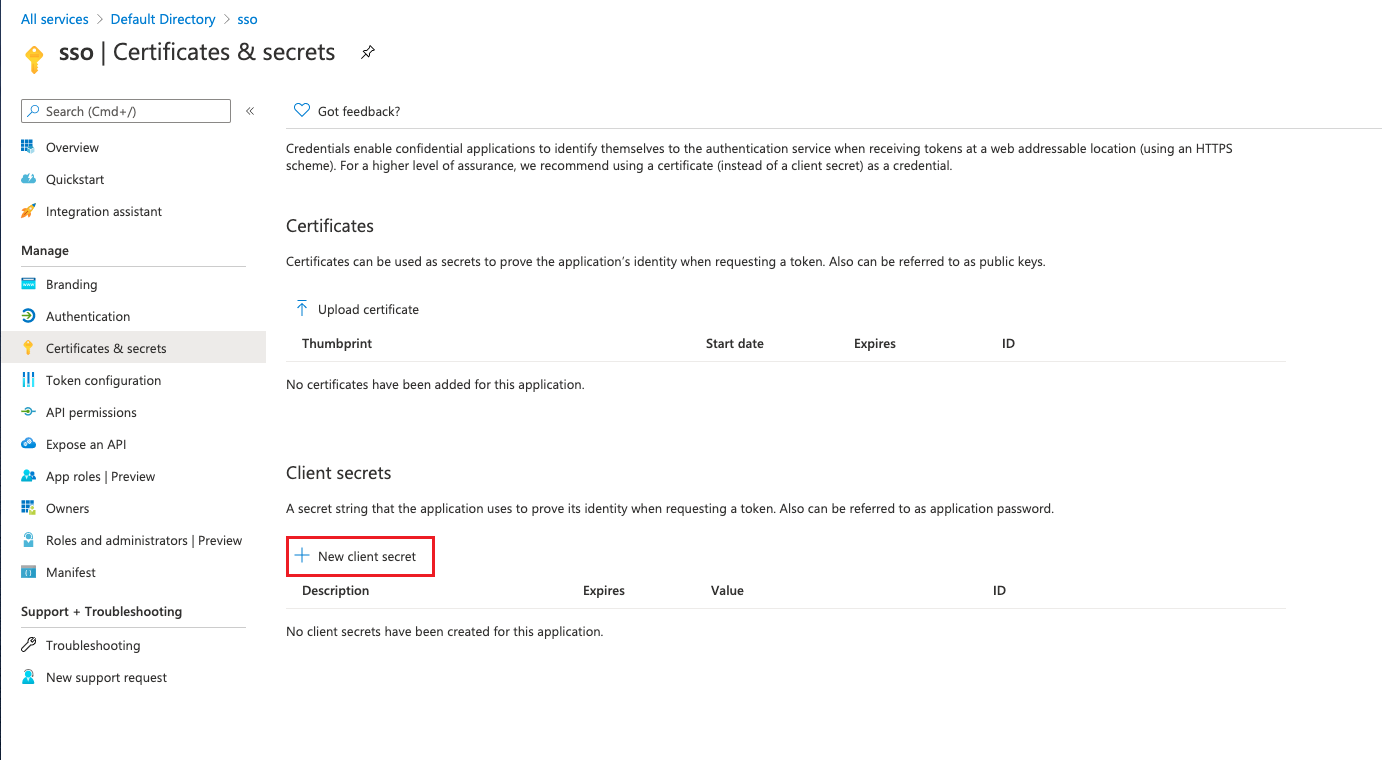
In the left menu item, select the Certificates & secrets menu item, new client secret, and get the ClientSecret after adding successfully.
Create Identity Provider for OAuth2
-
On the Identity Provider page, click the “Create” button at the top of the list to enter the Create Identity Provider page.
-
Configure the following parameters.
- Identity Provider attribution: Set the attribution range of the Identity Provider. When the Identity Provider belongs to the system, that is, all users in the system can use the Identity Provider to log in to the platform. When the Identity Provider belongs to the domain, only the users in the domain can use the Identity Provider to log in to the platform. In the Domain View, the Identity Provider belongs to the domain administrator’s domain.
- Name: The name of the Identity Provider.
- Authentication protocol: select “OAuth2”.
- Authentication type: Support Lark, Dingtalk, WeCom, etc.
- When the authentication type is Lark.
- AppId: the id of the application. Please see How to get Lark related parameters?
- Secret: the key of the app, generated by Lark open platform when creating the app.
- When the authentication type is Dingtalk.
- AppId: Id identifier of the app. Please see How to get Dingtalk related parameters?
- AppSecret: the key of the app, which is generated by the Dingtalk open platform when creating the authorization of the app with the sweep code.
- When the authentication type is WeCom.
- Enterprise ID: used to identify the enterprise. Please see How to get WebCom related parameters?
- AgentID: Id of the application.
- Secret: the key of the application.
- User attribution target Domain: you need to set this parameter only after you check the box to create users automatically. When the Identity Provider belongs to the domain, the user belongs to the same domain as the Identity Provider, and cannot be changed.
Advanced configuration: hidden by default, can be configured according to requirements.
- Default project: Set the default project for users who log in through the Identity Provider of OAuth2 authentication protocol and are automatically created in the platform to join.
- Default role: Set the default role joined by users who log in through the Identity Provider of OAuth2 authentication protocol and created automatically in the platform.
How to get Lark related parameters?
Description
For more, please see the Lark Developer Documentation
-
Enterprise users (no admin user required) login to Lark Developer Platform .
-
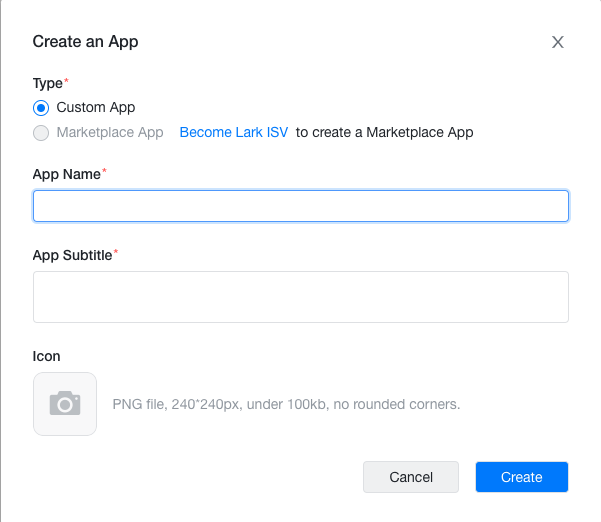
On the Developer Console page, create a Custom app.
-
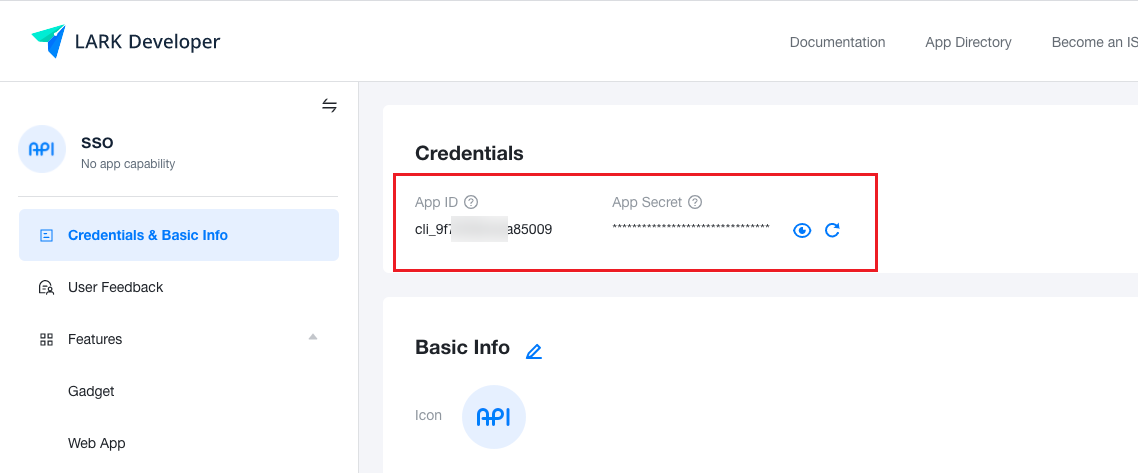
Get the application credentials in the “Credentials & Basic Info” page of the new application.
-
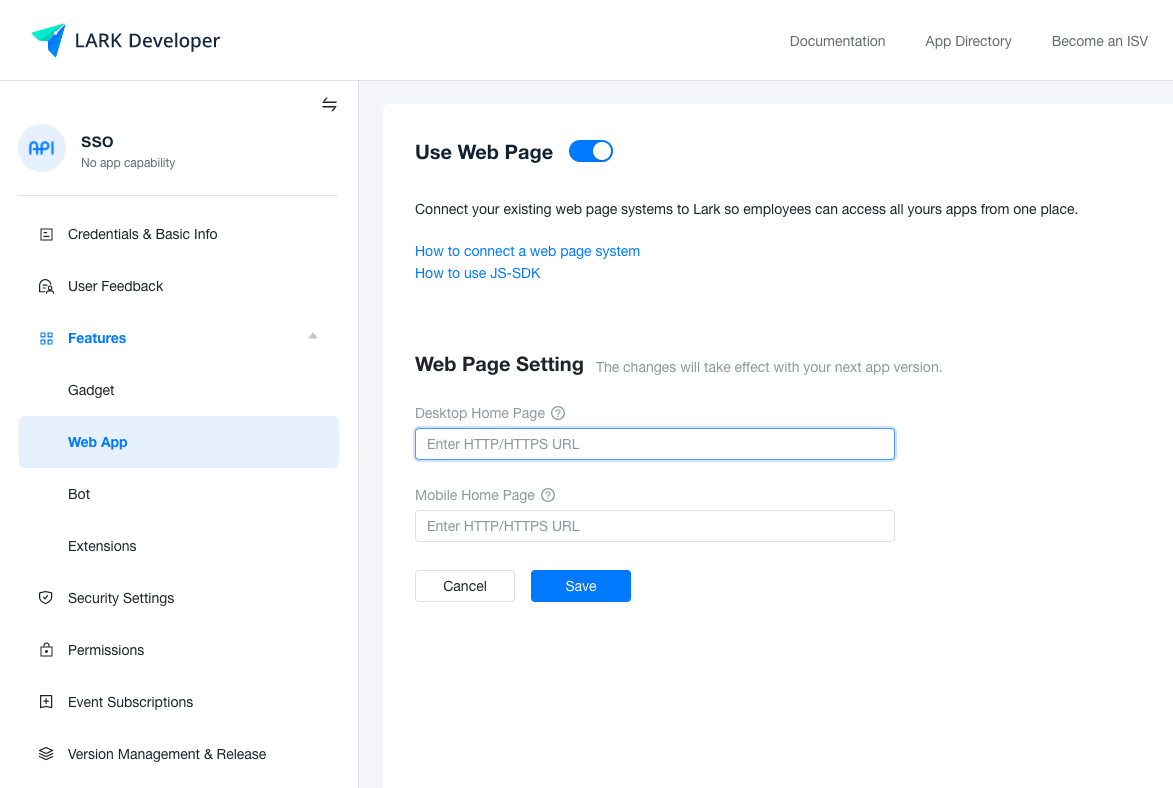
Enable the web page in the Features - Web App Page and add the access address of the platform to the home page of the desktop version in the web page configuration.
-
Configure the callback address or domain name “https://
/api/v1/auth/ssologin” in the redirect URL in the Security Settings. Description
- Set the platform to domain access, set the access domain in Global Settings - Console Address.
- The platform’s callback address can be viewed on the OneCloud platform Identity Provider page.
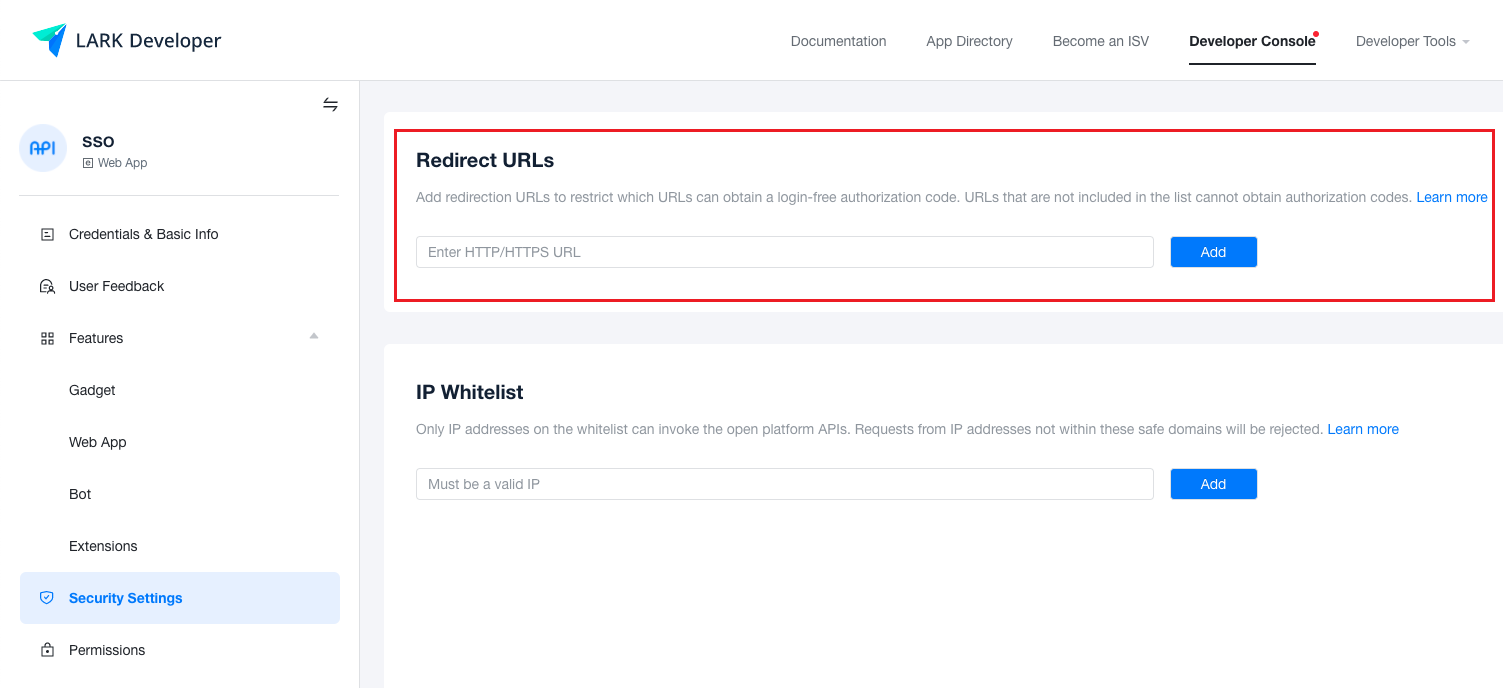
-
Add permissions to the application as needed in Permissions Page, at least “Obtain user email information”, “Access user’s phone number”, “Obtain users' userid”, “Access user basic information from the contact”, “Obtain user’s union id”.

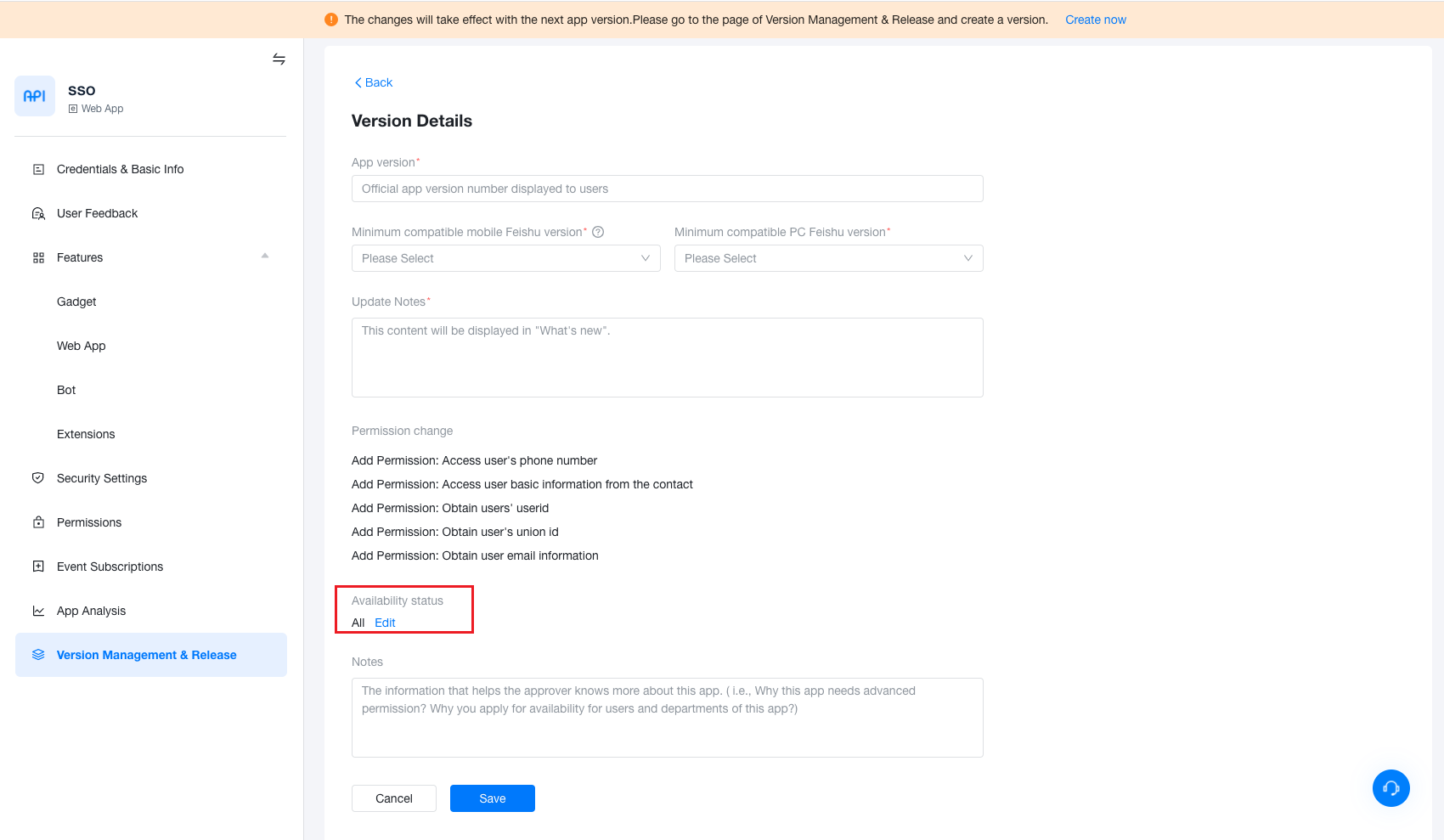
-
On the Version Management & Release page, create a version, configure the relevant information, note that the availability status is set to “All Employees” or the organization to which the application applies, and click the “Save” button to wait for the administrator to review and publish the application.
How to get Dingtalk related parameters?
Description
For more information, please see the Dingtalk website documentation
-
Login to Dingtalk Open Platform as administrator.
-
Create a code login application authorization in the Mobile Access Application - QR Login page on the “Application Development” page.
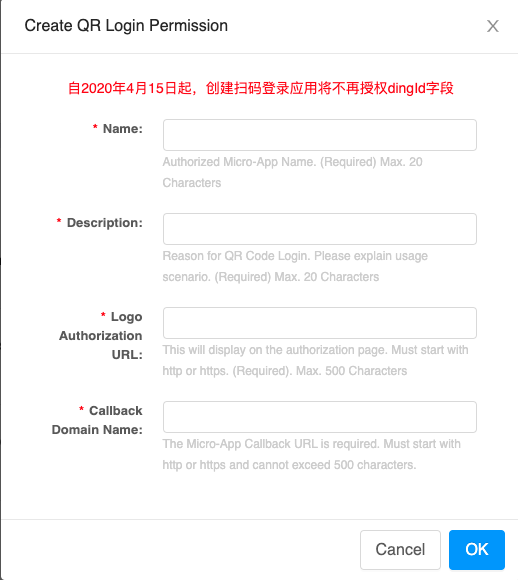
-
Configure the callback domain as “https://
/api/v1/auth/ssologin”. Description
- Set the platform to domain access, set the access domain in the global settings - console address.
- The platform’s callback address can be viewed on the OneCloud platform Identity Provider page.
-
After the creation, you can get the corresponding AppId and AppSecret.

How to get WebCom related parameters?
-
Login to WeCom Admin Console as administrator user
-
Get the enterprise ID from the top - My Company page.

-
Under the top - Application Management tab, select Application - Create Self-Built Application and configure the application logo, name, application description and visibility range.
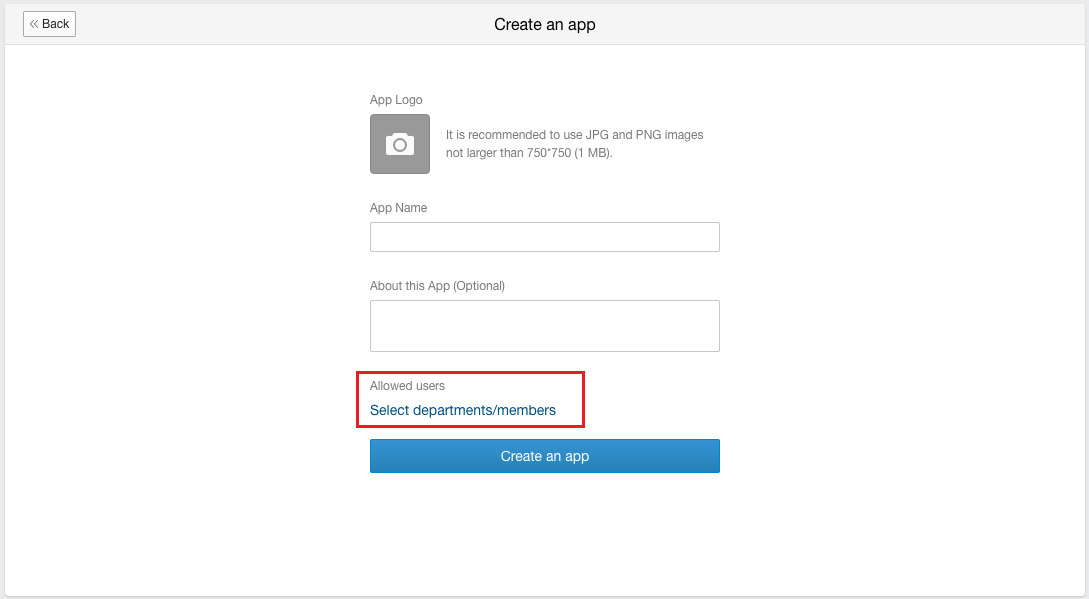
-
Set the authorization callback domain of the web page to the domain address in the Developer Interface - Authorization Login.
Description
- Set the platform to be accessed as a domain name and set the access domain to https://<domain_name> in Global Settings - Console Address.
- You can view the platform’s callback address in the OneCloud platform Identity Provider page, in WeCom you only need to fill in the domain name.
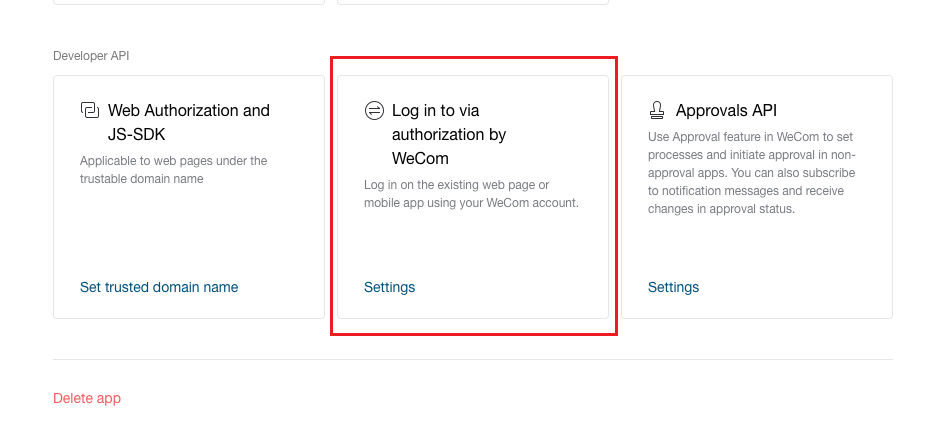
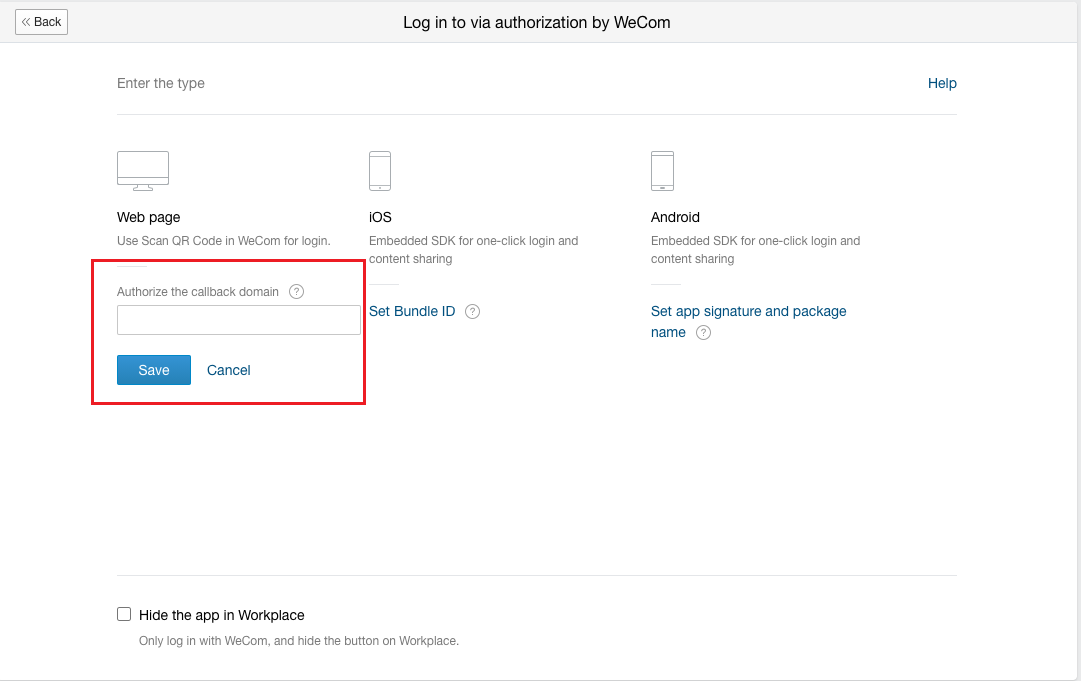
-
Get the AgentId and Secret information in the application details.
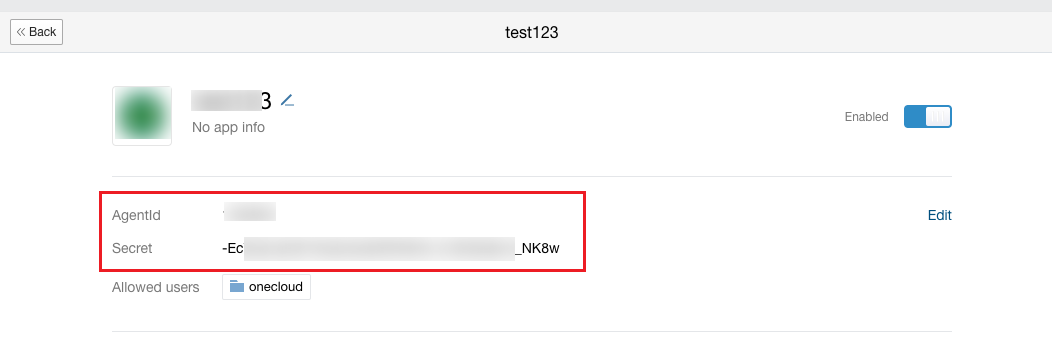
Modify configuration
This function is used to modify the configuration information of the Identity Provider, only the disabled state of the Identity Provider supports modification of the configuration. Please see the corresponding Create Identity Provider section for the configuration parameters of different authentication types.
Note
- The Identity Provider of SQL authentication protocol does not support modification of the configuration.
- On the Identity Provider page, click the “Modify Configuration” button on the right column of the disabled Identity Provider to enter the Modify Configuration page.
- Modify the parameters of the Identity Provider for different authentication types, and click the “OK” button after the modification is completed.
Enable Identity Provider
This function is used to enable the “disabled” state of the Identity Provider.
Note
- The Identity Provider of SQL authentication protocol does not support enable.
Enable
- On the Identity Providers page, click the “More” button in the action bar to the right of the disabled Identity Provider, and select the “Enable” menu item to bring up the action confirmation dialog.
- Click the “OK” button to enable the Identity Provider.
Batch Enable
- Check one or more identity provider in the Identity Provider list, click the**_“Batch Action”_** button at the top of the list, select the drop-down menu **_“Enable”_** menu item, and the operation confirmation dialog box pops up.
- Click the “OK” button to enable the Identity Provider.
Disable Identity Provider
This function is used to disable the Identity Provider in the “enabled” state.
Note
- The Identity Provider of SQL authentication protocol does not support disabling.
- When the Identity Provider is disabled, users under the Identity Provider cannot log in to the system.
- On the Identity Provider page, click the “More” button in the action bar to the right of the enabled Identity Provider, and select the “Disable” menu item to bring up the action confirmation dialog. Click the “OK” button to disable the Identity Provider.
Batch Disable
- Check one or more identity provider in the Identity Providers list, click the**_“Batch Action”_** button above the list, select the drop-down menu **_“Disable”_** menu item, and the operation confirmation dialog box pops up.
- Click the “OK” button to disable the Identity Provider.
Note
Delete Identity Provider
This function is used to delete the Identity Provider.
Note
- The Identity Provider of SQL authentication protocol does not support deletion.
- When the Identity Provider does not support automatic user creation and is used as a secondary Identity Provider, it can be deleted as long as the Identity Provider is disabled.
- When the Identity Provider supports automatic user creation, there are two cases.
- When the user belongs to the domain for the existing system domain, as long as the Identity Provider can be disabled to delete the Identity Provider and the users and groups under the Identity Provider.
- When the user belongs to an empty domain that is automatically created, you need to have no items under the domain automatically created by the Identity Provider, and the Identity Provider is disabled before you can delete the Identity Provider that is automatically created by the Identity Provider domain, users, and groups.
Delete
- In the Identity Provider page, click the “Delete” button on the right side of the disabled Identity Provider to bring up the action confirmation dialog. Click the “OK” button to complete the operation.
Batch Delete
- Check one or more identity provider in the Identity Provider list, click the**_“Batch Action”_** button above the list, select the drop-down menu **_“Delete”_** menu item, and the operation confirmation dialog box pops up.
- Click the “OK” button to complete the operation.
View Identity Provider Details
This function is used to view the details of the Identity Provider.
- In the Identity Provider page, click the Identity Provider Name item to enter the Identity Provider Details page.
- The top menu item of the details page supports the management of the Identity Provider.
- View the following information.
- Basic Information: Including Cloud ID, ID, name, status, item, Identity Provider attribution, enable status, synchronization status, automatic user creation, user attribution domain, authentication protocol, authentication type, synchronization time, created at, updated at, and description.
- Configuration information: Different authentication types display different configuration information.
- IDP source data: Only SAML support, support for downloading IDP source data.
- Resource statistics: Including the number of groups, users, projects, roles, and permissions under the Identity Provider.
View operation log
This function is used to view the log information of the operations related to the Identity Provider.
- On the Identity Provider details page, click the Operation Log tab to enter the Operation Log page.
- Load More Logs: In the Operation Logs page, the list shows 20 operation logs by default. To view more operation logs, click the “Load More” button to get more log information.
- View Log Details: Click the “View” button on the right column of the operation log to view the log details. Copy details are supported.
- View logs of specified time period: If you want to view the operation logs of a certain time period, set the specific date in the start date and end date at the top right of the list to query the log information of the specified time period.
- Export logs: Currently, only the logs displayed on this page are supported to be exported. Click the upper-right corner of
 icon, set the export data column in the pop-up export data dialog, and click the “OK” button to export the logs.
icon, set the export data column in the pop-up export data dialog, and click the “OK” button to export the logs.