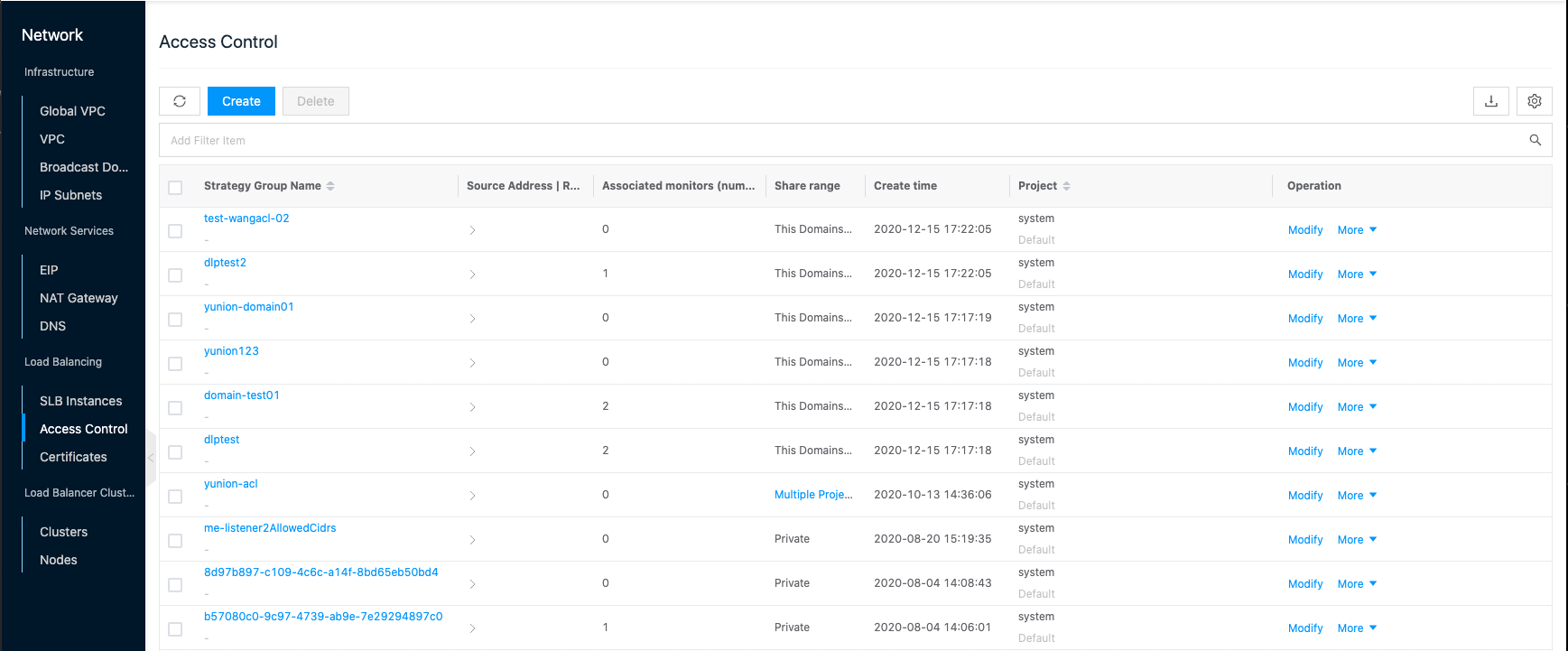
Access Control
Access control is used to set the IP whitelist or IP blacklist for accessing load balancing. Only IP address range can be set in the access control policy group, and you can set whether to enable access control when configuring load balancing instance listening, and set access whitelist or blacklist for specific access control policy group.
Access control source.
- Synchronize the access control bound by the listeners on the instance on the public cloud and automatically add a record in the access control cache, and the synchronized down access control is shared by this domain by default.
- Create access control policy groups on the cloud management platform.
Entry: In the cloud management platform click on the top left corner of  navigation menu, and click “Network/Load Balancing/Access Control” menu item in the left menu bar that pops up to enter the access control page.
navigation menu, and click “Network/Load Balancing/Access Control” menu item in the left menu bar that pops up to enter the access control page.
Create Access Control
This function is used to create an access control policy group.
- Click the “Create” button at the top of the list to bring up the Create Access Control dialog box.
- Set the following parameters.
- Specify item: Administrators and domain administrators need to specify the item to which the access control belongs when creating a new access control.
- Access Control Policy Group Name: Set the name of the access control policy group.
- Batch add IP address: Add the IP address and IP address segment of the source address in the access control policy group, etc.
- Each line is an IP address or IP address segment. IP address such as 192.168.1.1, IP address segment such as 192.168.1.0/24.
- IP address and remarks are separated by |, such as 192.168.1.0/24| Remarks, remarks information is optional.
- Click “OK” button to complete the operation.
Modify Access Control
This function is used to modify the IP address range of the access control policy group.
- Click the “Modify” button on the right operation column of the access control policy group to bring up the Modify Access Control dialog box.
- Modify the batch conditional IP addresses.
- Each row is an IP address or IP address segment. IP address such as 192.168.1.1, IP address segment such as 192.168.1.0/24.
- IP address and remarks separated by |, such as 192.168.1.0/24| remarks, remarks information is optional.
- Click “OK” button to complete the operation.
Change Project
This function is used to change the item to which the access control belongs. The item can be changed only when the access control is private.
Individual access control change projects
- On the Access Control page, click the “More” button on the right action bar of the Access Control Policy Group, and select the drop-down menu “Change Project” menu item to bring up the Change Project dialog box.
- Modify the fields and items, click “OK” button.
Batch Change Projects
- Select one or more access control policy groups in the access control list, click the “Batch Action” button at the top of the list, and select the drop-down menu “Change Projects” menu item to bring up the Change Projects dialog box.
- Modify the domain and item, click “OK” button.
Set up sharing
This function is used to set the sharing status of the access control.
There are five types of sharing ranges for project resources.
- No sharing (private): I.e. project resources are available only to users of this project.
- Project Share-Partial (shared by multiple projects in this domain): I.e. project resources can be shared to specified projects (one or more) under the same domain, and only users under this project and the shared project can use the project resources.
- Project Sharing-All (shared by this domain): I.e. project resources can be shared to all projects under the domain, i.e. all users of the project’s domain can use the project resources.
- Domain sharing-part (Multiple Domains sharing): I.e. project resources can be shared to the specified domain (one or more), and only users under the domain where the project resources are located and the shared domain can use the project resources.
- Domain Share-All (Global share): I.e. project resources can be shared to all domains, i.e. all users in the system can use project resources.
Description
To set the conditions for domain sharing.
- Three-level Resource Hierarchy have been turned on in the OneCloud platform.
- The user is in the admin backend.
To set up project sharing.
- The user is in the admin backend or domain admin backend.
access control to set sharing
- On the Access Control page, click the “More” button on the right action bar of the Access Control Policy Group and select the drop-down menu “Set up sharing” menu item to bring up the Set up sharing dialog box.
- Configure the following parameters.
- When “No Sharing” is selected as the sharing scope, the sharing scope of project resources is private and only users of this project can use them.
- When the sharing scope is selected as “Project Sharing”, you need to select the projects that can be shared under this domain.
- When the project selects one or more projects under the same domain, the shared scope of the project resources is Project Shared - Part, and only the users under the project where the project resources are located and the shared project can use the project resources.
- When All is selected for the project, the shared scope of the project resource is Project Shared - All, and all users under the project’s domain can use the project resource.
- When the sharing scope is “Domain Sharing”, you need to select the shared domains.
- When one or more of the domains is selected, the sharing scope of the project resources is Domain Sharing - Partial, and only the users under the domain where the project resources are located and the shared domain can use the domain resources.
- When All is selected for the domain, the sharing scope of the project resource is Domain Shared-All, and all users in the system can use the project resource.
- Click the “OK” button to complete the operation.
Batch Set up sharing
The scope of sharing for multiple access control batch settings must be the same. Otherwise, set up separate shares for the access controls.
- Select one or more access control policy groups in the Access Control list, click the “Batch Action” button at the top of the list, and select the drop-down menu “Set up sharing” menu item to bring up the Set up sharing dialog box.
- Configure the following parameters.
- When “No Sharing” is selected as the sharing scope, the sharing scope of project resources is private and only users of this project can use them.
- When the sharing scope is selected as “Project Sharing”, you need to select the projects that can be shared under this domain.
- When the project selects one or more projects under the same domain, the shared scope of the project resources is Project Shared - Part, and only the users under the project where the project resources are located and the shared project can use the project resources.
- When All is selected for the project, the shared scope of the project resource is Project Shared - All, and all users under the project’s domain can use the project resource.
- When the sharing scope is “Domain Sharing”, you need to select the shared domains.
- When one or more of the domains is selected, the sharing scope of the project resources is Domain Sharing - Partial, and only the users under the domain where the project resources are located and the shared domain can use the domain resources.
- When All is selected for the domain, the sharing scope of the project resource is Domain Shared-All, and all users in the system can use the project resource.
- Click the “OK” button to complete the operation.
Delete Access Control
This function is used to delete the access control, which can only be deleted when the listeners associated with the access control policy group are 0.
- On the Access Control page, click the “Delete” button in the right column of the access control policy group to bring up the Delete Confirmation dialog box.
- Click the “OK” button to delete the access control policy group.
View Access Control Details
This function is used to view the access control details.
- On the Access Control page, click the Access Control Policy Group Name item to access the Access Control Details page.
- View the access control policy group Cloud ID, ID, name, status, domain, item, source address|description, created at, updated at, and description.
View the list of listeners associated with the access control
This function is used to view the list of listeners associated with the access control.
In the Access Control page, click the Access Control Policy Group Name item to enter the Access Control Details page. 2. Click the Listening tab to enter the Listening page. View the list of listeners associated with the access control.
View the access control cache list
There are two sources of cache lists.
- When you create a load balancing instance on the public cloud platform that uses the access control policy group on the OneCloud platform, the certificate will be cached to the public cloud platform.
- Synchronizing the load balancing access control policy group on the public cloud platform will synchronize the new access control policy group and cache records on the OneCloud platform.
In the Access Control page, click the Access Control Policy Group Name item to enter the Access Control Details page. 2. Click the Cache List tab to enter the Cache page. View the cache list information, including the access control policy group name, created at, updated at, project, platform, region, and cloud account.
Delete cache
This function is used to delete the access control of the corresponding account region on the public cloud, and can only be deleted when the listening associated with the access control is 0.
- On the Access Control page, click the Access Control Policy Group Name item to enter the Access Control Details page.
- Click the Cache List tab to enter the Cache page.
- Click the “Delete” button in the action column on the right side of the access control cache to bring up the action confirmation dialog box.
- Click the “OK” button to complete the operation.
View Operation Log
This function is used to view the log information of the operations related to the access control policy group.
- On the Access Control page, click the Access Control Policy Group Name item to enter the Access Control Details page.
- Click the Operation Log tab to enter the Operation Log page.
- Load More Logs: In the Operation Logs page, the list displays 20 operation logs by default. To view more operation logs, click the “Load More” button to get more logs.
- View Log Details: Click the “View” button on the right column of the operation log to view the log details. Copy details are supported.
- View logs of specified time period: If you want to view the operation logs of a certain time period, set the specific date in the start date and end date at the top right of the list to query the log information of the specified time period.
- Export logs: Currently, only the logs displayed on this page are supported to be exported. Click the upper-right corner of
 icon, set the export data column in the pop-up export data dialog, and click the “OK” button to export the logs.
icon, set the export data column in the pop-up export data dialog, and click the “OK” button to export the logs.